Why in News?
The recent killing of 26 tourists in Baisaran near Pahalgam by terrorists has brought the spotlight back on the persistent infiltration threats along the India-Pakistan border, particularly in the Jammu & Kashmir region.
The incident underscores the urgent need for a robust counter-infiltration grid, enhanced surveillance technology, and better border infrastructure.
What’s in Today’s Article?
- The Terrain and Tactical Challenges
- Infiltration - Patterns and Prevention
- Counter-Infiltration Measures
- Border Security During Winters
- The Way Forward
- Conclusion
The Terrain and Tactical Challenges:
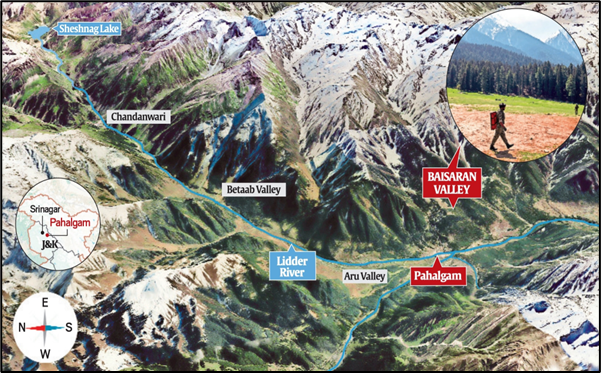
- Difficult terrain in Pir Panjal range:
- Dense forests with poor visibility (less than 100 meters).
- Rugged topography spanning hundreds of kilometres.
- Ideal hideouts for terrorists, making search and counter-operations difficult.
- For example, Baisaran, 6 km from Pahalgam, is accessible only on foot or by pony.
- The meadow is ringed by the densely forested Pir Panjal mountains that stretch far, toward Kokernag and Kishtwar to the south and Balatal and Sonamarg to the north.
- Security forces at risk:
- Over 50 army personnel have been martyred in counter-terror operations in areas like Poonch, Rajouri, Kathua, and Doda.
- Terrorists, often trained in Pakistan, operate in stealth, avoid local contact, and use encrypted communication tools.
Infiltration - Patterns and Prevention:
- India-Pakistan border profile:
- Total border length: 3,300+ km, of which ~1,000 km lies in J&K.
- Infiltration attempts have significantly decreased: Since the 2003 ceasefire agreement.
- Historical trends in infiltration:
- Infiltration in the 1990s was in the thousands annually.
- As of 2010, successful attempts dropped to 21% (52 out of 247).
- Current annual infiltration is estimated between 50–100.
- Pakistan-backed infiltration:
- Around 60% of terrorists killed in J&K in 2024 were Pakistani nationals.
- Source-based reports indicate three attackers in the Pahalgam incident were from Pakistan.
Counter-Infiltration Measures:
- Role of border fencing:
- Nearly the entire India-Pakistan border (including the LoC) is fenced.
- Fencing reduces infiltration but needs continuous repair and technological upgrades.
- Comprehensive Integrated Border Management System (CIBMS): Introduced post-Pathankot attack (2016), CIBMS uses advanced tech like -
- Thermal imagers, IR and laser sensors, aerostats,
- Radars, fibre-optic sensors, sonar for riverine borders.
- CIBMS challenges:
- Delays due to tech unavailability and planning issues.
- Project deadline shifted from Dec 2018 to Dec 2025.
- Riverine patch solutions remain underdeveloped.
Border Security During Winters:
- Weather-induced damage:
- One-third of the fence is damaged each winter due to snow up to 15 feet.
- Repairs take 3–4 months, leading to temporary security gaps.
- Operational difficulties:
- Inhospitable conditions: Sub-zero temperatures, fog, and rain affect alertness.
- Limited rest for soldiers: 1 night’s sleep in 3 days is common.
- Night vision and surveillance devices: Have limited operating hours and often lack power sources.
The Way Forward:
- Technological upgradation:
- Develop smart fences with real-time breach alerts.
- Enhance aerial surveillance and tunnel detection technology.
- Invest in all-weather surveillance
- Infrastructure investment:
- Build weather-resilient fences.
- Ensure power availability for surveillance equipment.
- Bolster manpower training and rest-rotation policies to maintain alertness.
Conclusion:
The Pahalgam terror attack reaffirms the continuing threat of cross-border terrorism in J&K and the urgent need to strengthen India's counter-infiltration infrastructure.
While efforts like the CIBMS and border fencing have shown results, gaps in implementation, weather challenges, and evolving terrorist tactics necessitate a comprehensive, technology-driven, and well-funded security strategy.









