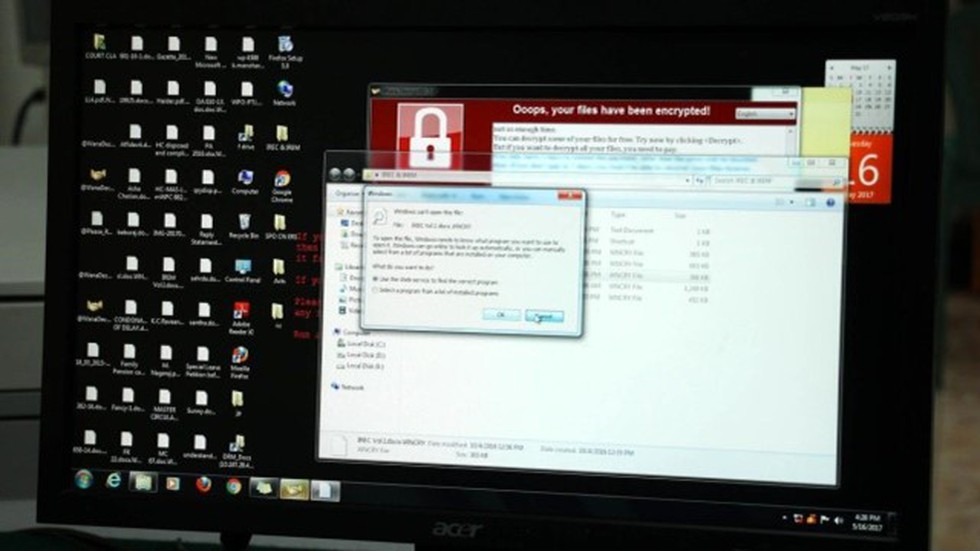
About Akira Ransomware:
- It is designed to encrypt data, create a ransomware note and delete Windows Shadow Volume copies on affected devices.
- The ransomware gets its name due to its ability to modify filenames of all encrypted files by appending them with the “.akira” extension.
How does Akira Ransomware work?
- The ransomware is designed to close processes or shut down Windows services that may keep it from encrypting files on the affected system.
- It uses VPN services, especially when users have not enabled two-factor authentication, to trick users into downloading malicious files.
- The ransomware also terminates active Windows services using the Windows Restart Manager API, preventing any interference with the encryption process.
- It is designed to not encrypt Program Data, Recycle Bin, Boot, System Volume information, and other folders instrumental in system stability.
- It also avoids modifying Windows system files with extensions like .syn. .msl and .exe.
- Once sensitive data is stolen and encrypted, the ransomware leaves behind a note named akira_readme.txt which includes information about the attack and the link to Akira’s leak and negotiation site.
- Each victim is given a unique negotiation password to be entered into the threat actor’s Tor site.
- Unlike other ransomware operations, this negotiation site just includes a chat system that the victim can use to communicate with the ransomware gang.
How does ransomware infect devices?
- Ransomware is typically spread through spear phishing emails that contain malicious attachments in the form of archived content (zip/rar) files.
- Other methods used to infect devices include drive-by-download, a cyber-attack that unintentionally downloads malicious code onto a device, and specially crafted web links in emails, clicking on which downloads malicious code.
- The ransomware reportedly also spreads through insecure Remote Desktop connections.