About Distributed Denial-of-Service (DDoS) Attack:
- A DDoS attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
- DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic.
- Exploited machines can include computers and other networked resources such as IoT devices.
- Unlike other kinds of cyberattacks, DDoS assaults don’t attempt to breach your security perimeter. Rather, a DDoS attack aims to make your website and servers unavailable to legitimate users.
- DDoS can also be used as a smokescreen for other malicious activities and to take down security appliances, breaching the target’s security perimeter.
- How does a DDoS attack work?
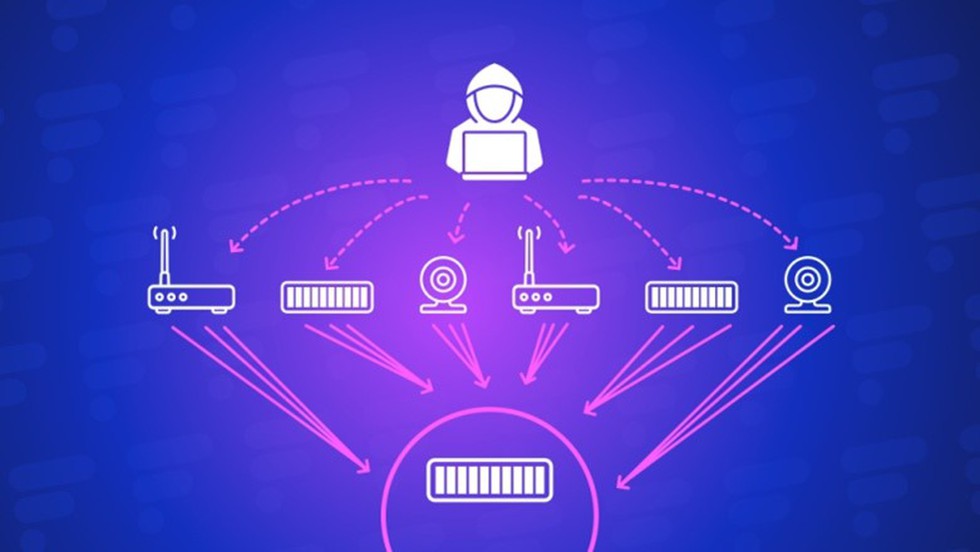
- DDoS attacks are carried out with networks of Internet-connected machines.
- These networks consist of computers and other devices (such as IoT devices) which have been infected with malware, allowing them to be controlled remotely by an attacker.
- These individual devices are referred to as bots(or zombies), and a group of bots is called a botnet.
- Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot.
- When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial of service to normal traffic.
DoS vs DDoS
- A DDoS attack is a subcategory of the more general denial-of-service (DoS) attack.
- In a DoS attack, a perpetrator uses a single Internet connection to either exploit a software vulnerability or flood a target with fake requests—usually in an attempt to exhaust server resources.
- On the other hand, DDoS attacks utilize thousands (even millions) of connected devices to fulfil its goal.