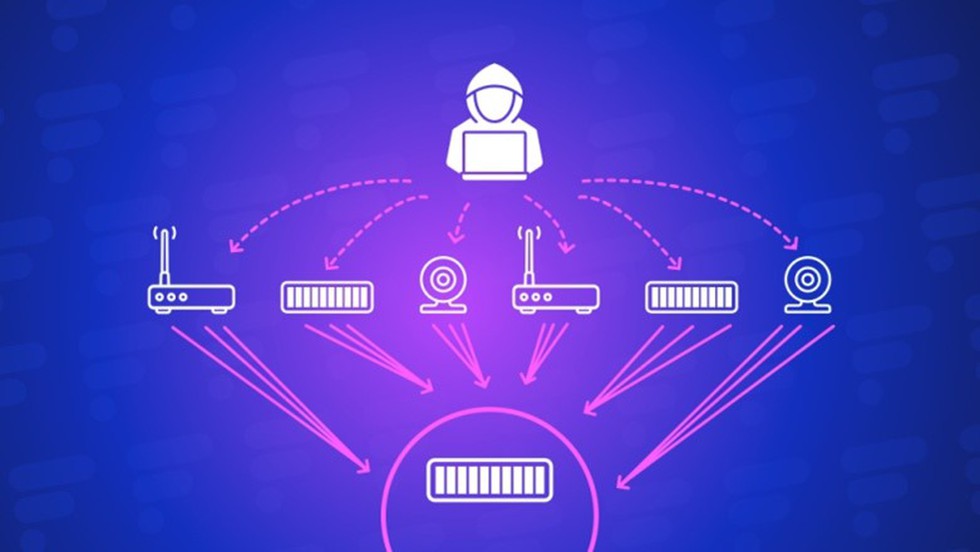
About Distributed Denial-of-Service (DDoS) Attack:
DoS vs DDoS
Gradual warming of temperatures obser...
Recently, the Ministry of Development...
A NASA PREFIRE polar mission is set t...
Following increasing reports of “digi...
Muria tribal farmer, who migrated fro...
Marble mined in Gujarat's Ambaji has ...
The Supreme Court recently held that ...
Venezuela is thought to be the first ...
China's latest scientific milestone, ...
At least seven members of a family, i...